In my previous blog we created a dynamic populated drop-down list with all available Rubrik SLA domain names. This drop-down list was used in a standard vRA IaaS request form when requesting a new virtual machine.
After doing some testing at my customers environment, we discovered that our current approach for facilitating backups with Rubrik through vRealize Automation was not efficient enough.
This was caused by the behavior of how Rubrik can include a virtual machine into backup. Before a newly deployed virtual machine is available for assigning a SLA domain name, it needs to be recognized by Rubrik. To be recognized by Rubrik, we needed to force a Rubrik discovery of vCenter objects after every virtual machine deployment with vRealize Automation.
This resulted in long virtual machine deployment times because every deployment needed to wait on a task for Rubrik discovery of vCenter objects. To make it even worse, multiple tasks for Rubrik discovery of vCenter objects get queued when more virtual machines are requested frequently or simultaneously. Eventually this resulted in failed virtual machine deployments because the vRO actions used in the Rubrik vRO workflows are receiving a time-out.
However, out-of-the-box, a Rubrik discovery of vCenter objects task is triggered a couple of times per hour. With the knowledge that you can assign a default SLA domain on vCenter objects (vCenter Server, vCenter Cluster or vCenter ESXi Host), we decided to change our backup strategy.
We are now assigning a default SLA domain name on the vCenter Cluster level, so every requested virtual machine with vRA will be automatically in backup. Instead of asking the SLA domain name on the the vRA request form, we are now offering a vRA Day2Operation to dynamically change the Rubrik SLA domain name. This blog reveals how we configured this vRA Day2Operation.
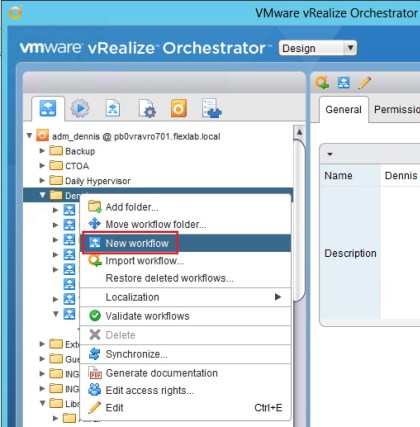
- First we created a copy/duplicate of the Rubrik vRO workflow “Rubrik Assign VM to SLA Domain”. Name this new workflow “Rubrik Change SLA Domain”.
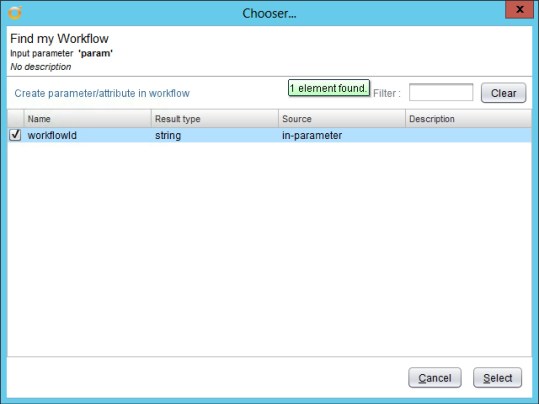
- Edit the “Rubrik Change SLA Domain” workflow. Go to the presentation tab and add a property of the type “predefined answers” to the input parameter “slaDomainName”.
- Assign the action “rubrikGetAllSLA” (The one we created in my previous blog post) as a value to this new property.
- Save the new workflow and it is ready to be used as a Day2Operation in vRealize Automation.

- Now create a resource action in vRA based on the newly created vRO workflow “Rubrik Change SLA Domain”.
- Next, publish the resource action and assign it to your entitlement.
- When you now select your provisioned virtual machines under Items in vRA, you will see your newly created Day2Operation “Rubrik Change SLA Domain”.

- Now lets test the new available vRA Day2Operation. After you select it, it will ask you for the new Rubrik SLA domain name. Make you choice, change the Rubrik SLA domain name of your virtual machine and click Submit.

- Thats’s it! You now have changed the Rubrik SLA domain name of your virtual machine. Enjoy consuming Rubrik through vRA.